Introduction:In 2018, the overall output value of China's security industry was about 709.6 billion yuan, of which the AI related software and hardware market reached 13.5 billion yuan, an increase of nearly 250% compared with 2017. It is expected that the market will maintain a high growth rate in 2019, and the growth rate will start to stabilize in 2020, the end of the 13th Five Year Plan, when the market size will reach 45.3 billion yuan.
In the past two years, AI technology has gradually come into reality from science fiction. AI is no longer a powerful AI steward who is about to be universal, or an overwhelming propaganda that robots are about to destroy mankind. AI has begun to be widely concerned as a new technology that has a real driving force for the industry.
When it comes to AI enabling industry, the most well-known one is AI mobile phone. Voice assistant, face recognition and unlocking, intelligent beauty, etc. have become the mainstream functions of mobile phones, but so far, AI has the best landingmarketNot the mobile phone industry, but based onvideoLarge security scenarios in the monitoring field.
Market size of security industry in 2018, and AI related software and hardware market size
Since the 13th Five Year Plan, the country has made great efforts to build a safe city and a bright project, and built an intelligent public security system based on camera monitoring network. Computer vision, video image analysis, natural language processing and other artificial intelligence technologies have found the best landing scenario, which has also brought new vitality to the security industry. In 2018, China's overall security industry output value was about 709.6 billion yuan, of which the AI related software and hardware market size reached 13.5 billion yuan, Compared with the growth of nearly 250% in 2017, it is estimated that the market will still maintain a high growth rate in 2019, and the growth rate will start to stabilize in 2020 by the end of the 13th Five Year Plan, when the market size can reach 45.3 billion yuan.
Public Securitybig dataThree pain points of application
In 2018, public security big data applications face three pain points. First, a large number of structured, unstructured and semi-structured data resources have been generated in the construction of public security informatization. The existing public security system can only simply apply structured data in data application, and most unstructured and semi-structured data do not play a role; Second, the construction of local public security databases is different, and most of them only stay at the level of standard databases and original databases, lacking valuable associations between data; Third, in most regions, only a few police types, such as anti-terrorism and anti drug, are carrying out intelligent application exploration, without forming an intelligent application network for all police types, and the ability of prediction, early warning and prevention is generally low.
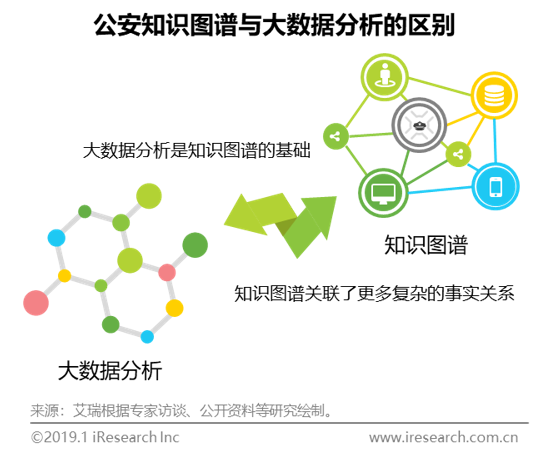
Definition of knowledge map and its difference from other analysis services
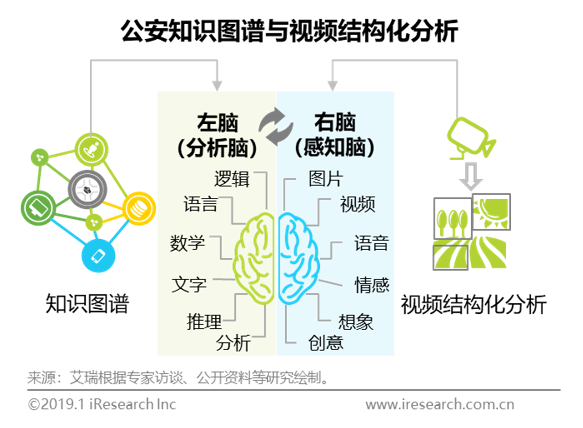
To solve the problem of data relevance, the construction of industry knowledge map has become the mainstream of the application of public security big data. Knowledge map is a technology to sort and organize data into a knowledge base. It is a kind of big data structure that can achieve higher quality, computable and computer understandable by applying semantic understanding technology, and is used to improve the search and query ability of data, information and intelligence. Knowledge map, big data analysis and video structured analysis belong to software application services, but there are obvious differences. Video structured analysis is to process unstructured video data into machine recognizable data sets through computer vision technology. It is one of the data sources upstream of the knowledge map. It can be said that video structured analysis realizes some problems solved by human eyes and human right brain visual areas, The knowledge map is more like the left brain of human beings, which constructs and invokes knowledge by analyzing the information stored in the right brain; Big data analysis realizes data structure and association. Knowledge atlas is a practical cognitive application formed by connecting the "point, line and plane" data association with the complex non simple directional relationship in the reality of things through semantic understanding on the basis of big data analysis.
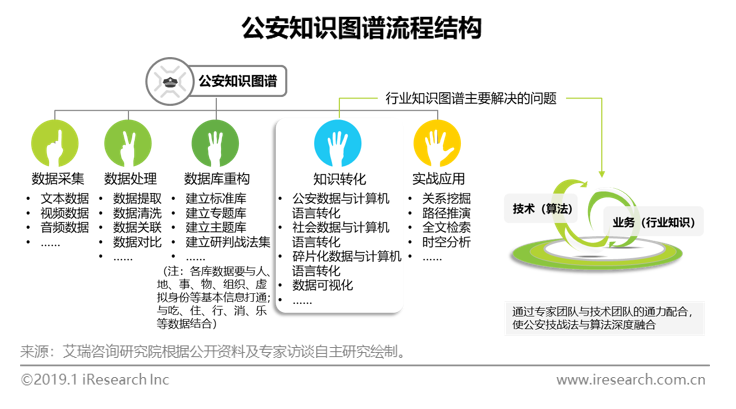
The Significance and Construction of Public Security Knowledge Map
In the field of public security, how to transform the practical experience and technical algorithm accumulated by the police for many years is the biggest industry difficulty, and also the main problem to be solved by the knowledge map. Through five steps of data collection, data processing, database reconstruction, knowledge transformation and practical application, the public security knowledge map uses distributed storage, association algorithm, semantic reasoning and other technologies, as well as a large number of public security expert teams and technicians to achieve the deep integration of technology and business. At present, under the map structure of "one billion data nodes and ten billion related edges", the application of public security knowledge map that can realize second level query is an excellent product standard in China. With the strong promotion of the State Council and the Ministry of Public Security, there will be a larger scale and higher data set knowledge map application in the future.
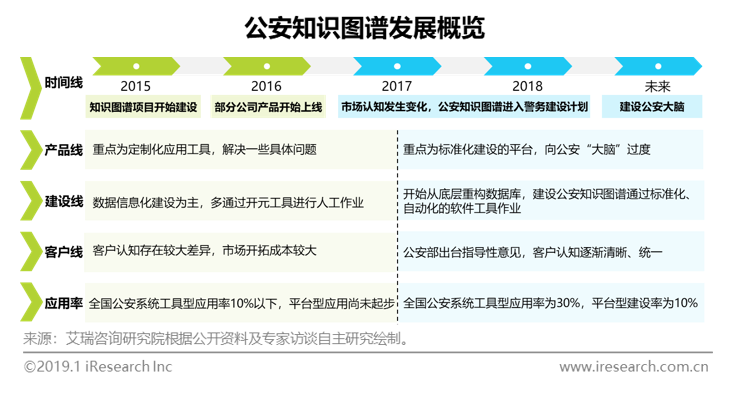
The Development and Evolution of Public Security Knowledge Map
The construction of public security knowledge map started late, with a few big data analysis in 2015companyIt began to try to build. At the initial stage, it appeared in the form of small and specific tools and software. Data association was mostly achieved through manual tagging, which was inefficient and of limited value. Its application rate nationwide was only less than 10%. After the technical development and implementation practice, as well as the unification of internal technical standards and the automation of service tools, the market cognition has changed since 2017. With the relevant guidance issued by the Ministry of Public Security in 2018, the public security system at all levels has gradually clarified and unified their understanding of the public security knowledge map. More large-scale projects based on the platform at the basic level have been put into construction, and the maintenance and application of existing projects have continued, In 2018, the application rate of the tool type public security knowledge map will be 30%, and the platform type construction rate will reach 10%. iResearch will continue to be optimistic about its development.
Report connection:http://report.iresearch.cn/report_pdf.aspx?id=3327